About Me
I'm a security professional with seven years of experience in Cloud Security. Currently at Adobe, I focus on detecting cloud threats at scale. I hold a Master's in Information Security from Johns Hopkins University and a Bachelor's in Computer Science from Vellore Institute of Technology, India.
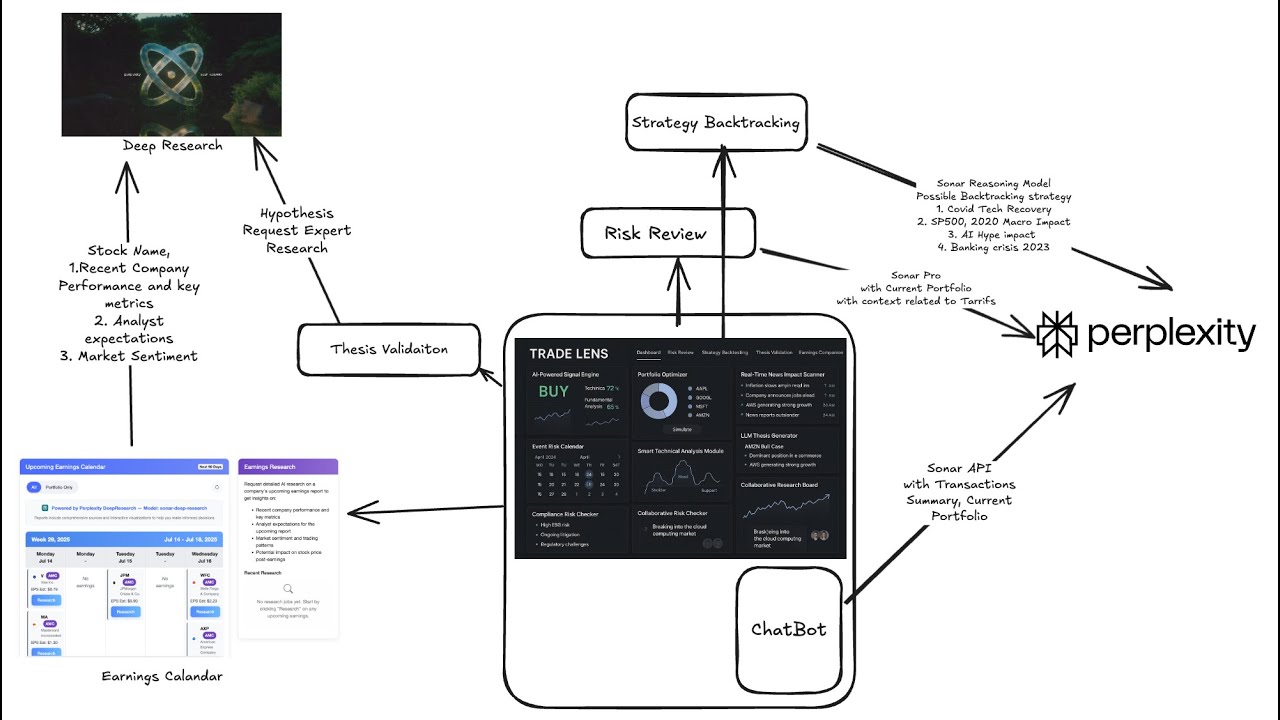
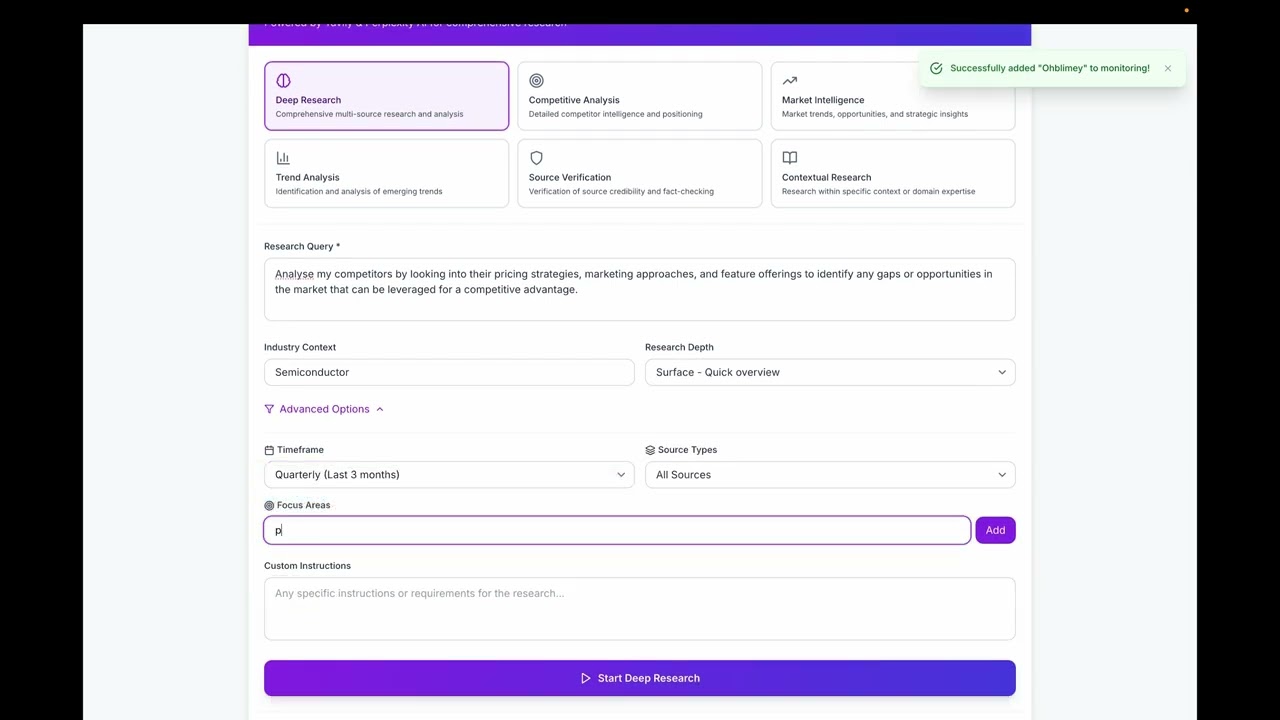
I am passionate about designing large-scale secure systems with a focus on Cloud Security, Application Security,
and Threat Intelligence. My expertise includes detecting cloud threats at scale, developing automated security pipelines,
and implementing proactive threat hunting frameworks. I've worked extensively with AWS environments, aligning cloud
infrastructure with enterprise security policies and strengthening security controls.
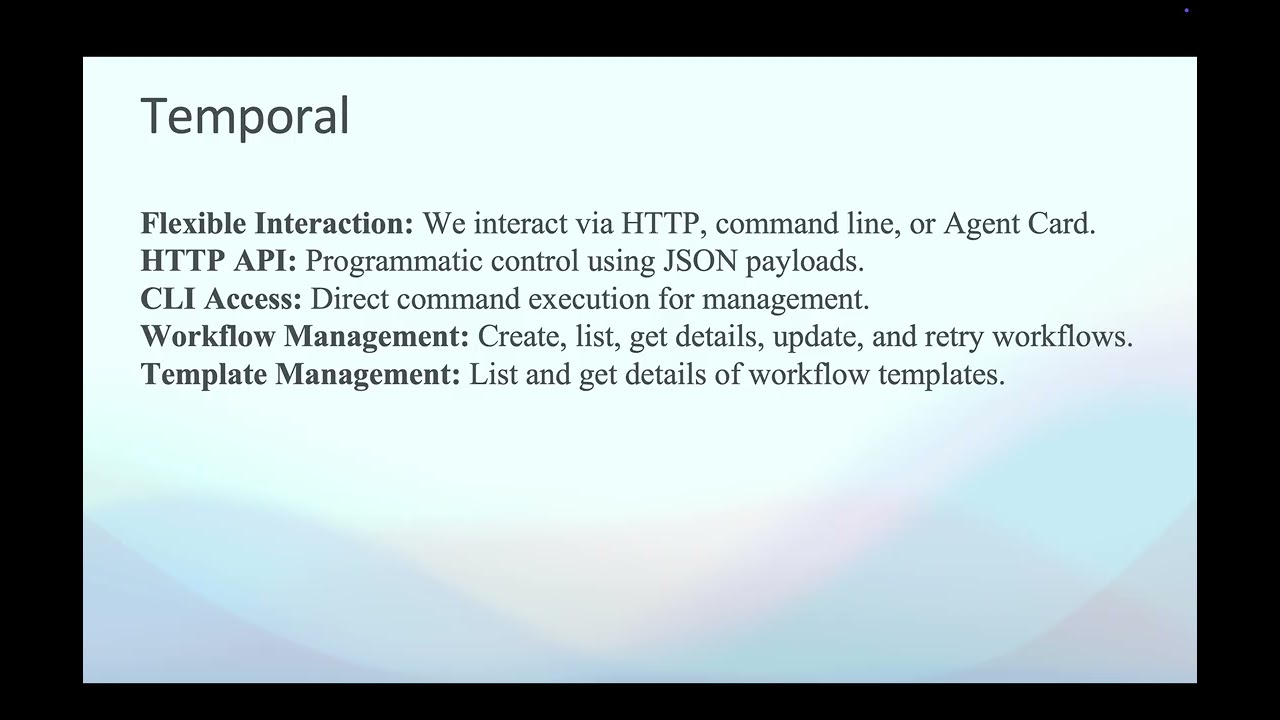
My recent focus has been on Large Language Models (LLMs), particularly in the area of
LLM security. I'm deeply interested in understanding and mitigating security vulnerabilities
in these systems, including sophisticated attacks like jailbreaking and prompt injection.
I work on developing robust defenses against adversarial techniques that attempt to bypass
safety guardrails in LLMs, while also exploring the broader implications of these technologies
for cybersecurity.
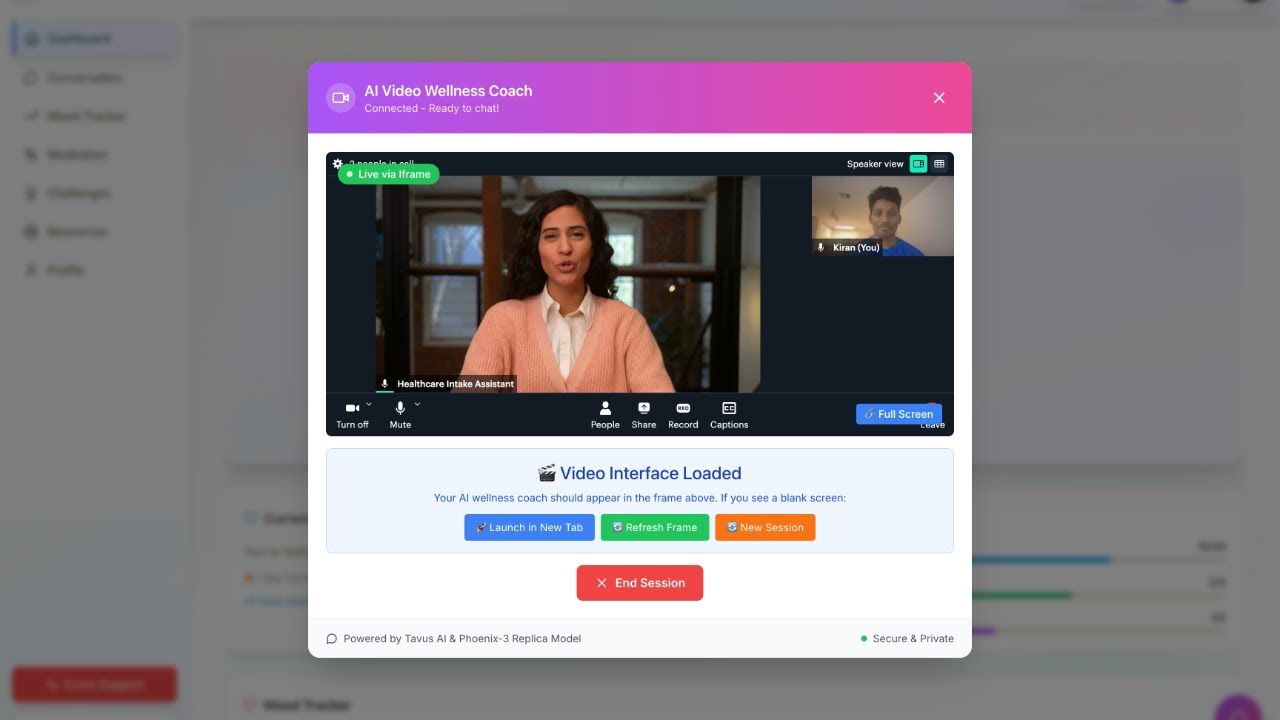
This intersection of AI and security presents fascinating challenges that combine my expertise
in threat detection with emerging technologies.
I actively contribute to open-source projects and regularly participate in Capture the Flag competitions and Hackathbox
challenges with the handle
backdoorcipher.
Recent Conference Talks
I regularly speak at security conferences on topics related to cloud security, threat detection, and emerging technologies:












For more information about my speaking engagements, visit my speaker profile.
Guest Lecture Invitation
Certifications
I hold several industry-recognized certifications that validate my expertise in cybersecurity and cloud security:



Technical Publications
I regularly publish technical articles on enterprise security architecture and cloud security best practices:
- Designing Effective Data Security Schemas - A comprehensive guide to implementing robust data classification frameworks that balance security requirements with operational efficiency in enterprise environments.
- Practicing Proper DMZ and Firewall Hygiene - An in-depth analysis of network segmentation strategies and firewall configuration best practices to protect critical infrastructure from emerging threats.
Academic Publications
My research has been published in academic journals focusing on security vulnerabilities and cloud threat analysis:
Journal of Computer Technology, 2016
Journal of Computational and Theoretical Nanoscience, 2019
Timeline
Hackathons & CTF Competitions









In the News
Featured in SVCSI post about CyberWarrior-Adobe CTF at SVCC 2025: Read the article
Featured in SVCSI post about SVCC 2025 Industry Sessions: Read the article
Featured YouTube Videos
Watch my tech talks and tutorials on various security topics: